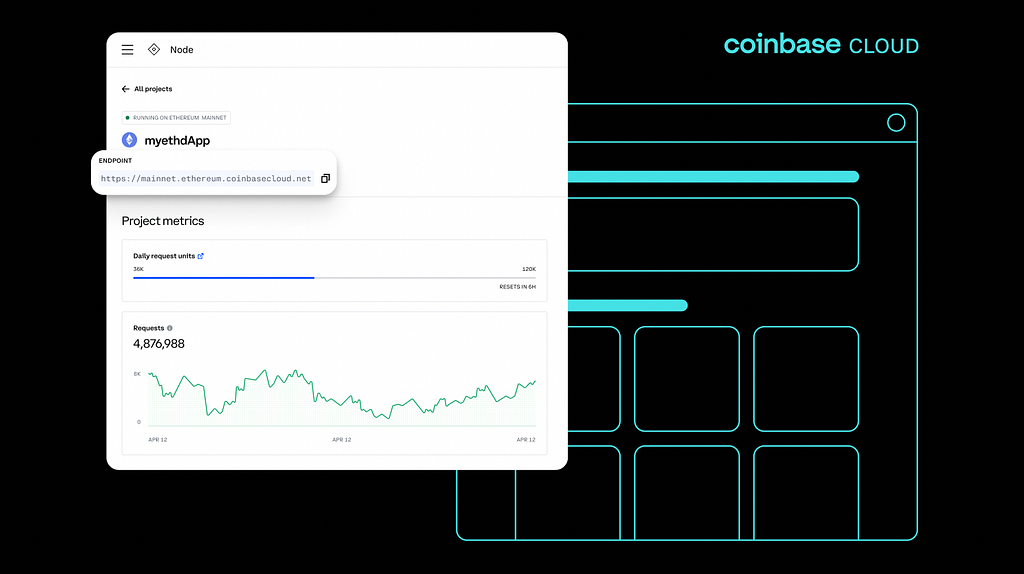
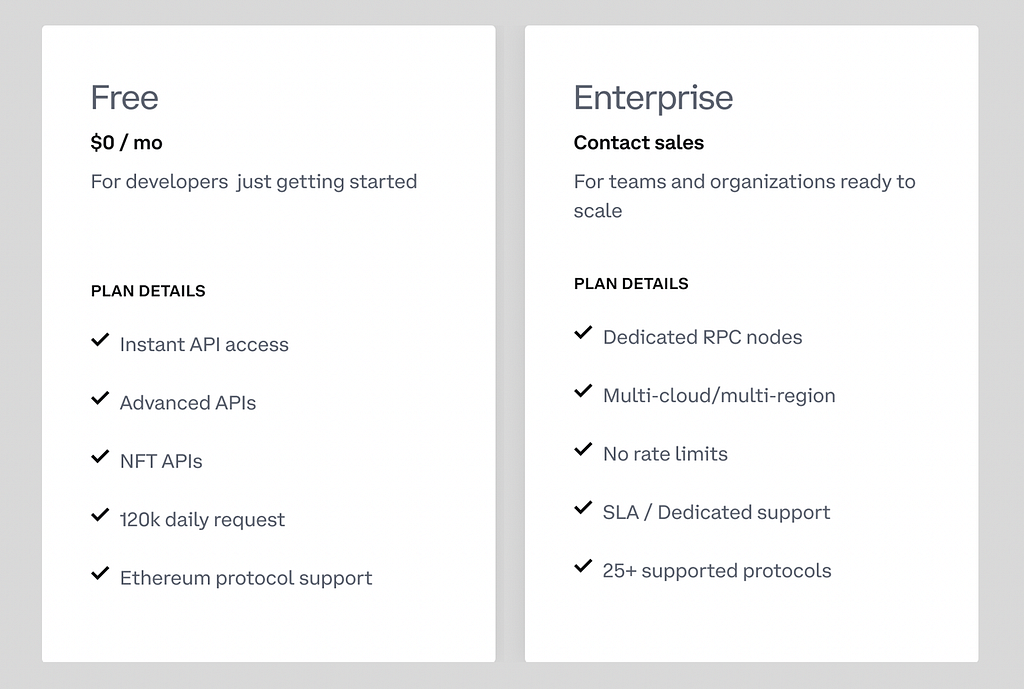
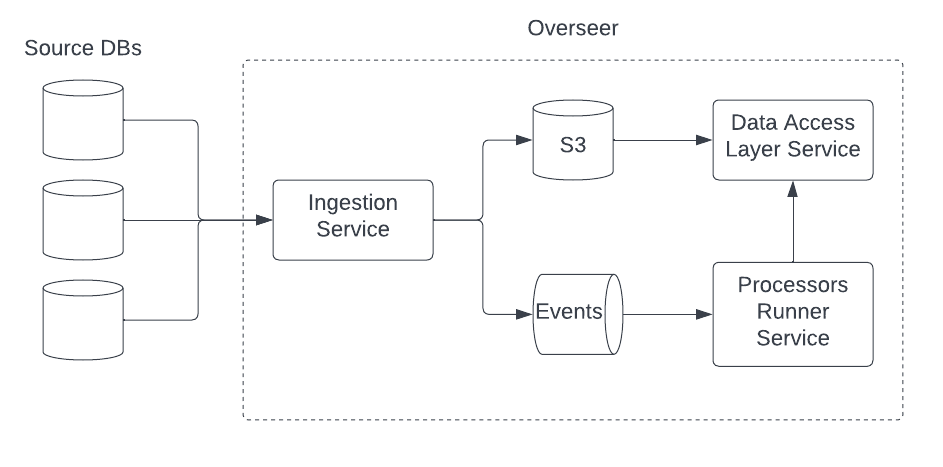
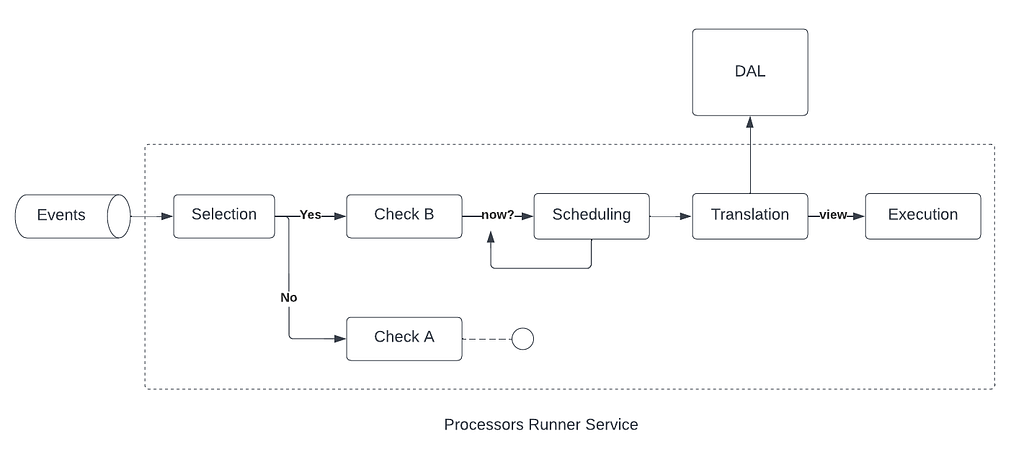
In response to the Wall Street Journal

Tl:dr Earlier today, the Wall Street Journal published an article highlighting client-driven activities, which they seem to confuse with proprietary trading.
Unlike many of our competitors, Coinbase does not operate a proprietary trading business or act as a market maker. In fact, one of the competitive strengths of our Institutional Prime platform is our agency only trading model, where we act only on behalf of our clients. As a result, our incentives and our clients’ incentives are aligned by design.
Coinbase does, from time to time, purchase cryptocurrency as principal, including for our corporate treasury and operational purposes*. We do not view this as proprietary trading because its purpose is not for Coinbase to benefit from short-term increases in value of the cryptocurrency being traded.
Expanding institutional participation in web3 beyond HODLing
As more institutions have become interested in investing in crypto, we are rolling out new solutions to help. One way we intend to serve our institutional clients is through a small newly formed team called Coinbase Risk Solutions (CRS).
CRS offers solutions to sophisticated institutional investors who seek exposure to the crypto asset class. Some of these investors are still getting familiar with crypto markets and ask for our assistance in managing risks and participating in protocols. The goal of CRS is to expand institutional participation in web3 beyond HODLing.
In doing this, we are following a well trodden path on Wall Street where financial services firms provide clients multiple ways to get exposure to new asset classes and manage certain risks. We have tools and policies in place that mirror best practices in the financial services industry and are designed to manage conflicts of interest.
*In December of 2021 we accurately outlined our investment activity in digital assets as part of our testimony to Congress, which you can find here.
In response to the Wall Street Journal was originally published in The Coinbase Blog on Medium, where people are continuing the conversation by highlighting and responding to this story.