Meet the refreshed Coinbase Card: More crypto rewards ¹, no more transaction fees²
By Muneeb Imtiaz, Senior Product Manager
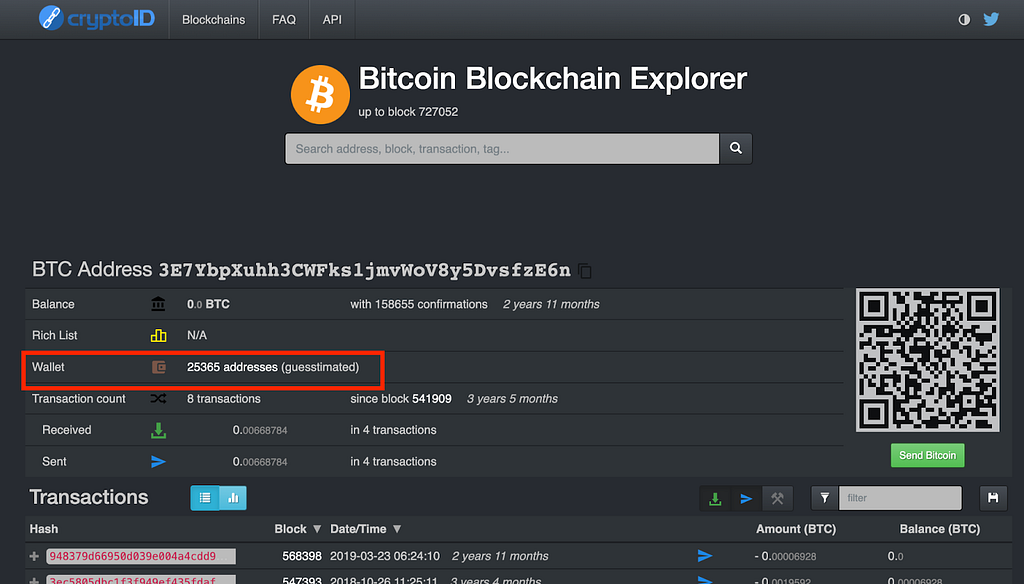
At Coinbase, we’re reimagining the crypto spending and earning experience by building products that are safe, trusted, and easy-to-use. That’s why we’re enhancing Coinbase Card to give customers more flexibility than ever. Through Coinbase Card’s upcoming rotating rewards structure, customers will be able to earn a wider variety of crypto rewards to diversify their crypto portfolio. We’re also removing the transaction fee for all crypto spending and allowing customers to get paid into Coinbase with no fees on deposits so they can easily fund their card in any currency³. With millions of transactions to date, we plan to remove the waitlist later this spring to allow all US* customers to sign up for Coinbase Card.
Rotating rewards
Customers love earning crypto rewards, and tell us that Coinbase Card encourages them to explore and learn more about different cryptocurrencies. Soon, customers will have the opportunity to easily earn new assets from a rotating list of crypto rewards just by swiping their card. With the rotating rewards structure, customers will continue to earn up to 4% back on every purchase with up-and-coming crypto assets like The Graph (GRT) or popular assets such as Bitcoin (BTC)⁴. Rewards will have an expiration date. If a customer doesn’t select a reward when the next rotation is launched, we’ll automatically give them the reward with the highest crypto-back rate so they can diversify their earnings.

No more fees
Customers love the ability to conveniently spend crypto. While most customers spend USDC, they tell us that the crypto spending fees on non-USDC assets are a barrier to using crypto for everyday purchases. That’s why we’re removing the transaction fee for crypto spending on the Coinbase Card, starting today⁵. By removing this fee, customers now have more flexibility to spend crypto or cash.
Easy funding
As customers spend more, we want to make it easier for them to fund purchases for their card. We’re now giving customers more options to easily load up their card, so they can get some or all of their paycheck deposited into Coinbase with no fees on direct deposits. This means that customers can now receive their paycheck in fiat or crypto and spend crypto without fees, moving more of their financial life into the cryptoeconomy.
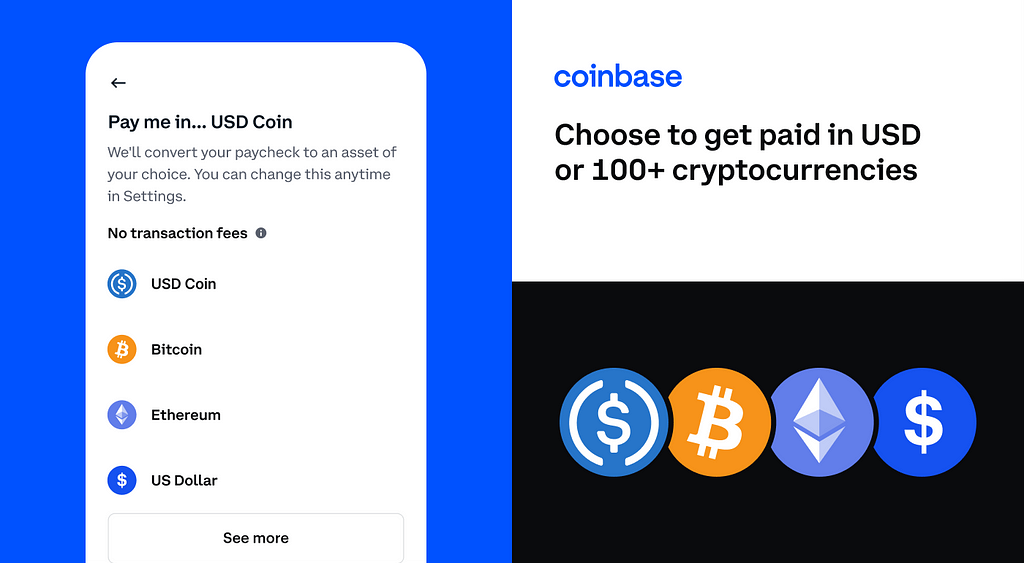
Unlimited rewards⁶
Customers can continue to earn unlimited crypto rewards and use their Coinbase Card anywhere Visa® debit cards are accepted. From earning rewards on morning coffee to monthly gym memberships, Coinbase Card continues to be a richly rewarding experience for everyday spending.
With no credit check⁷ or requirement to stake your assets to become eligible, we’re making it easy to sign up and start earning crypto rewards. Join the waitlist for Coinbase Card and we’ll notify you as soon as you’re next in line.
*Coinbase Card will be available to all eligible customers in the US, excluding Hawaii.
¹ Crypto rewards is an optional Coinbase offer.
²No Coinbase transaction fees but a spread applies when customers buy, sell, or trade crypto assets.
³ If you choose to be paid in crypto, Coinbase will automatically convert your paycheck from US dollars to crypto with no transaction fees. See terms.
⁴ Reward options may vary. Check your app for the most updated rewards.
⁵ While this feature is free, other fees may be associated with the card. See Cardholder Agreement for details.
⁶ Spending limits apply, see terms.
⁷ Important information for opening a Card account: To help the federal government fight the funding of terrorism and money laundering activities, the USA PATRIOT Act requires all financial institutions and their third parties to obtain, verify, and record information that identifies each person who opens a Card account. What this means for you: When you open a Card account, we will ask for your name, address, date of birth, and other information that will allow us to identify you. We may also ask to see your driver’s license or other identifying documents.
Rewards are for illustrative purposes only, actual reward options may vary.
The Coinbase Card is issued by MetaBank®, N.A., Member FDIC, pursuant to a license from Visa U.S.A. Inc. The Coinbase Card is powered by Marqeta. You may use Coinbase Card to make purchases anywhere Visa Debit cards are accepted.
Meet the refreshed Coinbase Card: More crypto rewards ¹, no more transaction fees² was originally published in The Coinbase Blog on Medium, where people are continuing the conversation by highlighting and responding to this story.