Security PSA: Sha Zhu Pan (Pig Butchering) Investment Scams
Tl;dr Coinbase has seen a concerning increase in fraudulent cryptocurrency investment platforms that are sourcing victims through connections on dating apps and social media. We are encouraging our users to be vigilant against this type of social engineering scam.
The Coinbase Security team has previously submitted the domains in this blog, in addition to several other related domains, to Google Safe Browsing for alerting users when browsing to these sites.

By Coinbase Global Investigations and Threat Intelligence
Coinbase works closely with law enforcement partners across the globe to protect our customers from an array of targeted cyber attacks. Recently, a noteworthy increase in scams purporting to be foreign exchanges or crypto trading platforms that are spread by scammers met on dating apps has been reported. While investment scams and romance scams are not unique to the cryptocurrency ecosystem, the irreversible nature of cryptocurrency transactions can make these scams devastating. This scheme is particularly effective because it relies on a scammer building trust with their victim sometimes over a long time period of weeks or months.
The scam typically follows this chain of events:
- Victims are contacted through social media, have matched with the scammer on a dating app, or have been contacted on instant messaging applications.
- The scammer encourages the victim to migrate their conversation to an encrypted messaging service, such as WhatsApp or WeChat, sometimes communicating for weeks or months before mentioning an investment opportunity.
- The scammer typically claims they have received great financial returns from a cryptocurrency trading or mining platform and convince their victim to co-invest with them or teach them how to trade successfully.
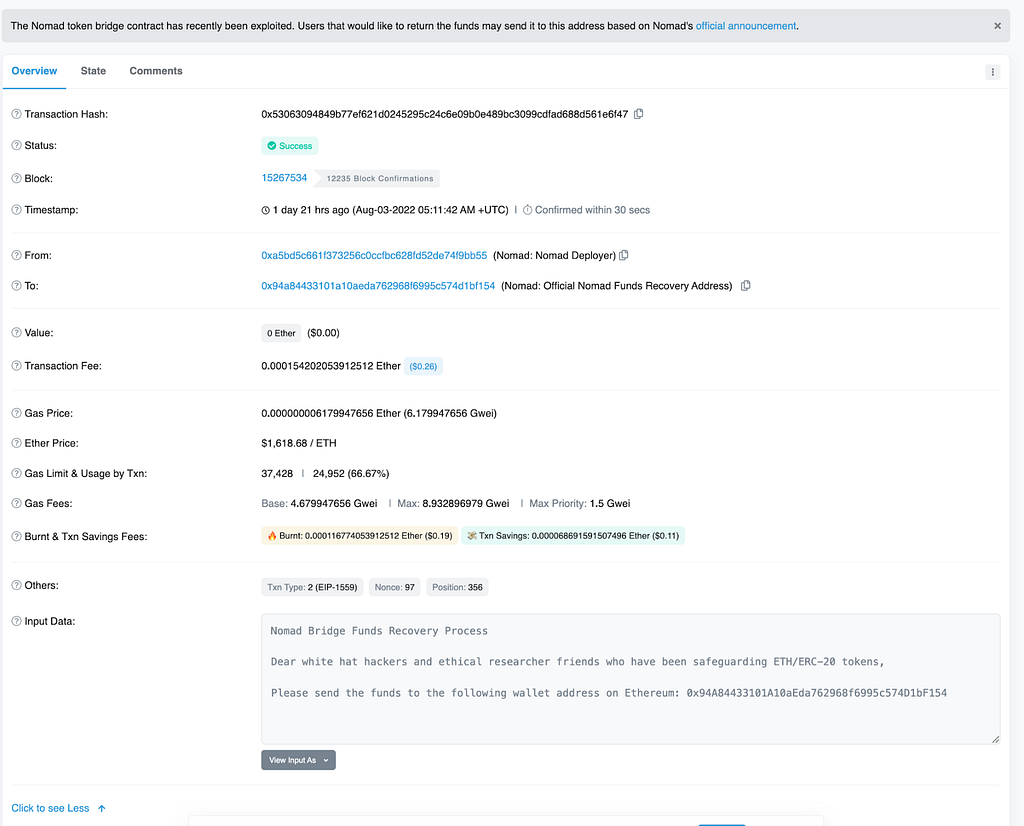
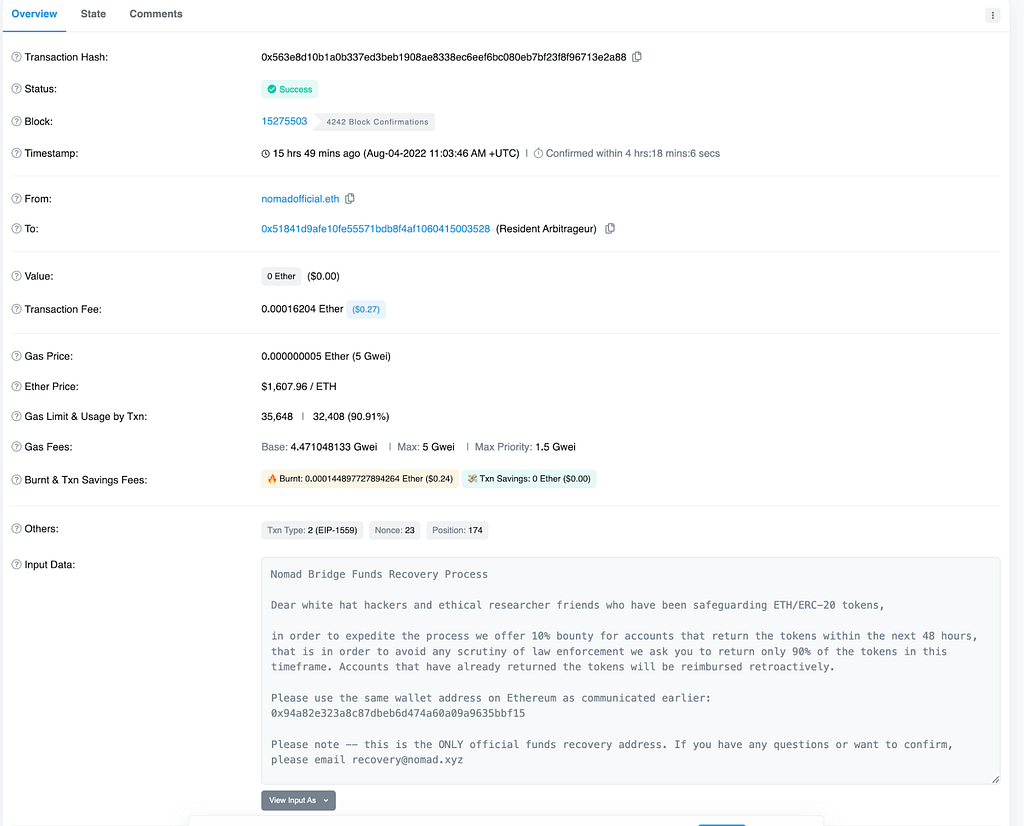
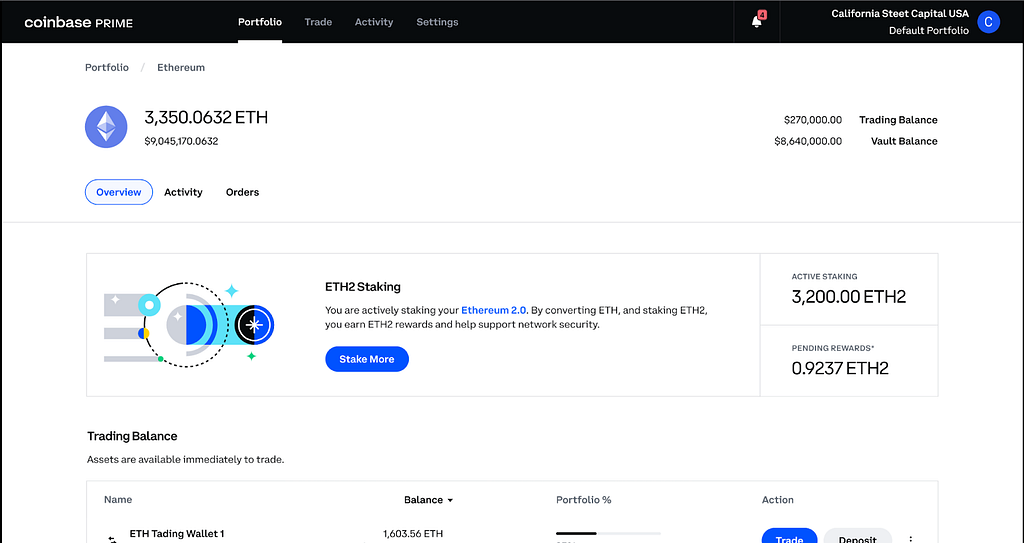
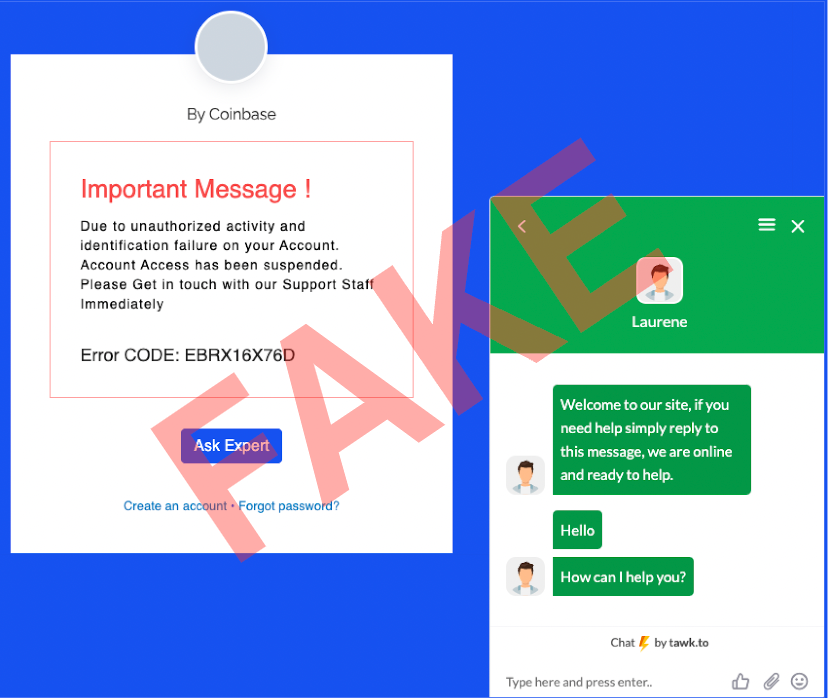
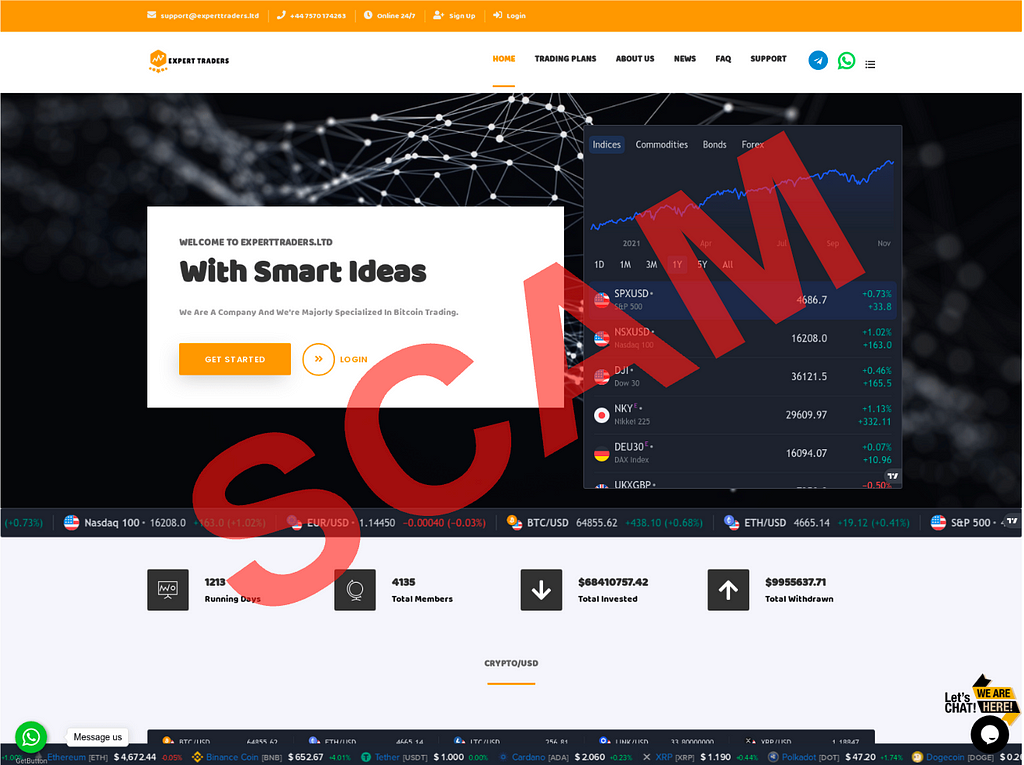
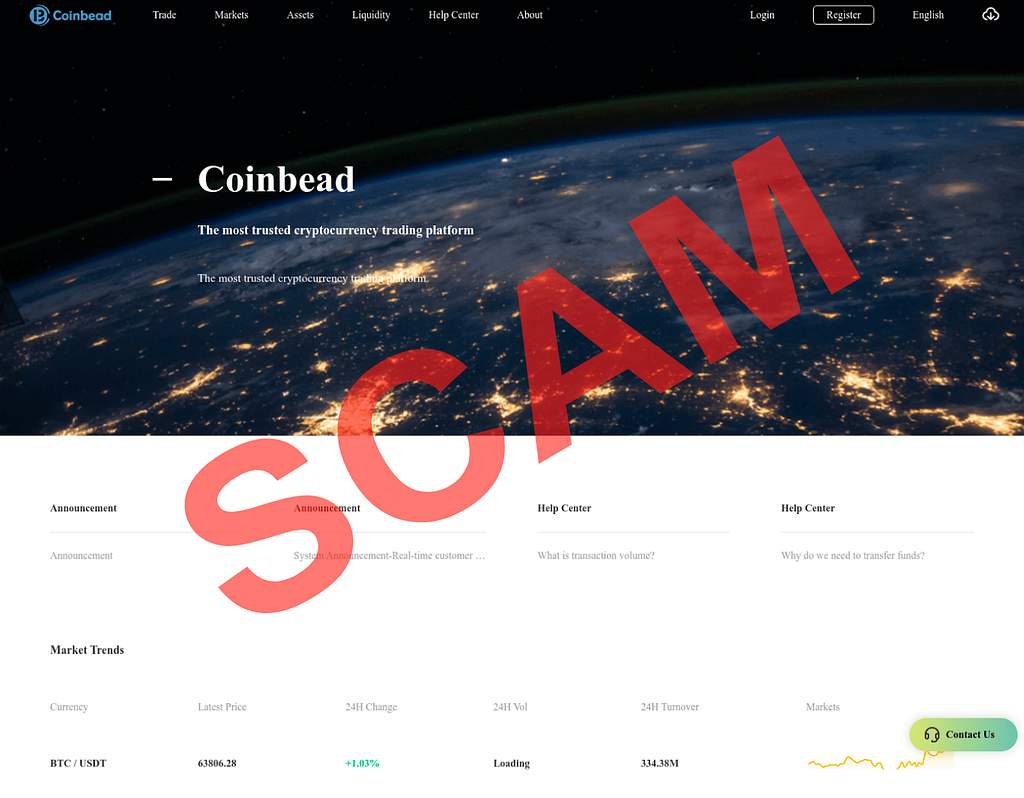
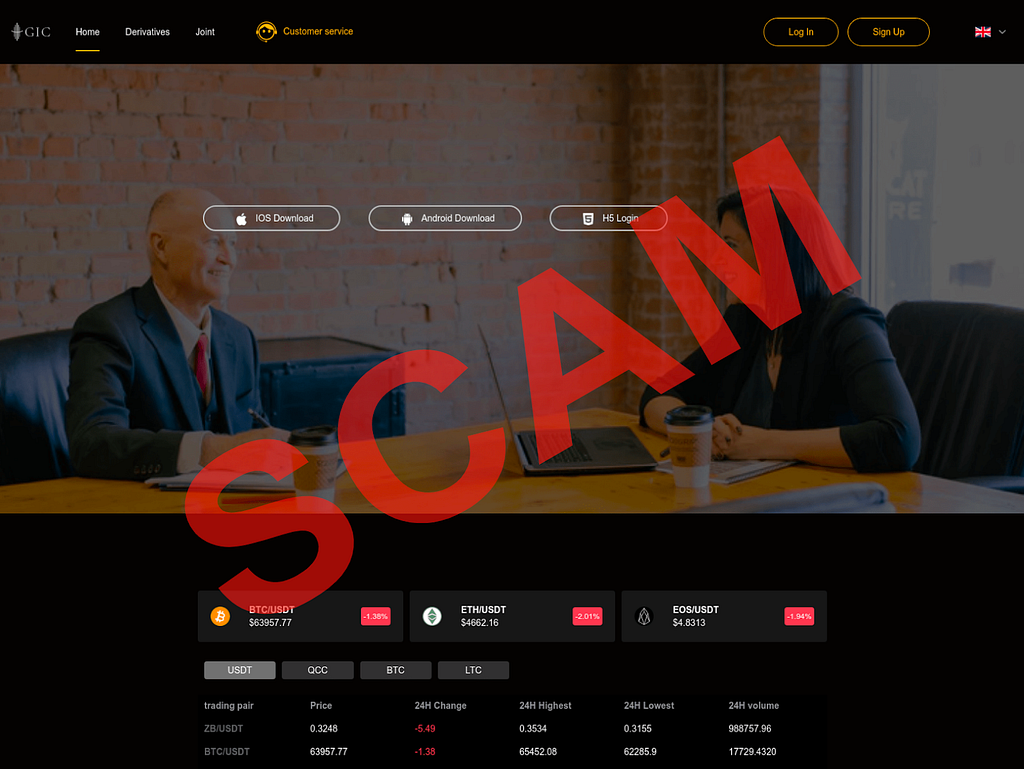
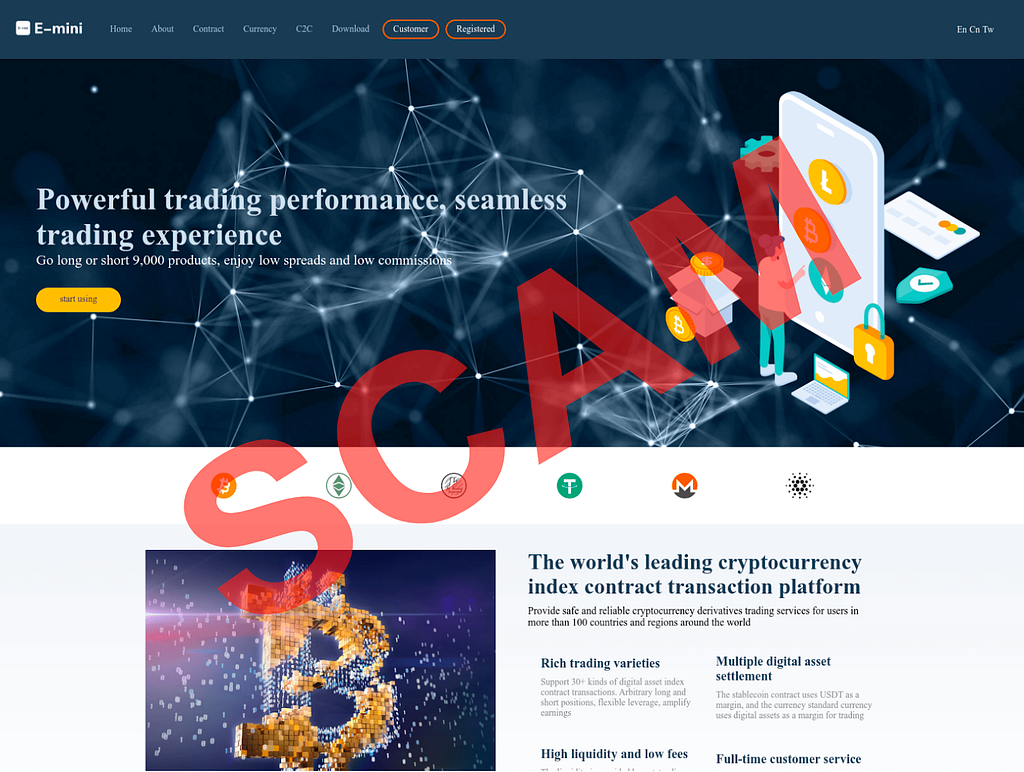
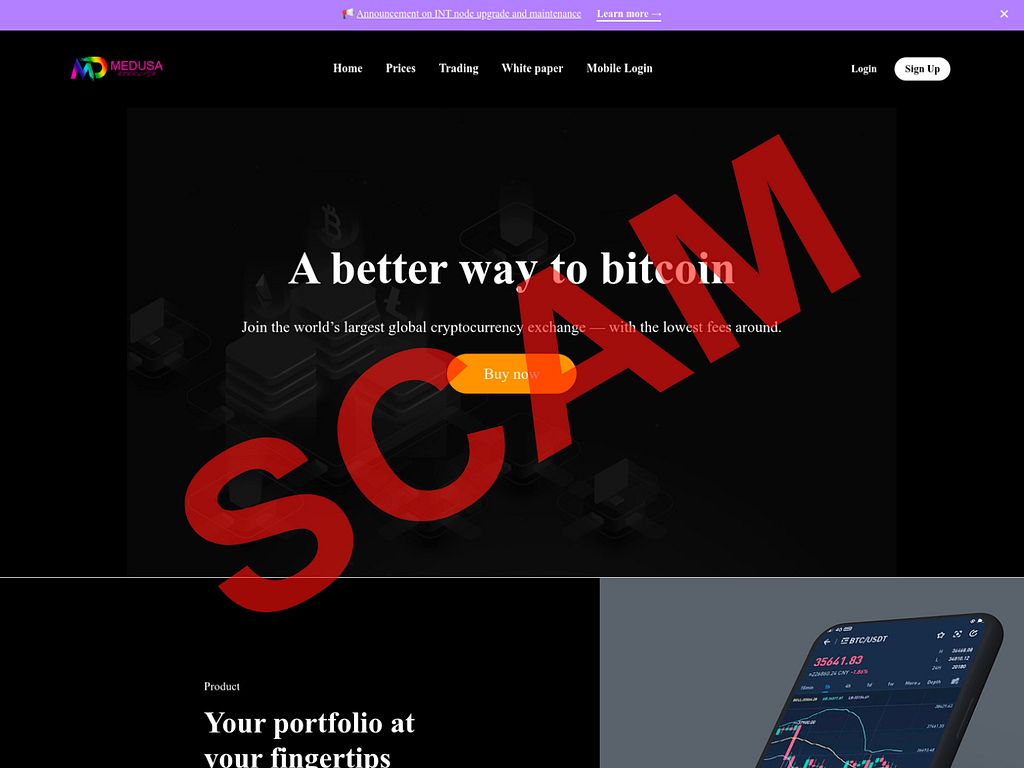
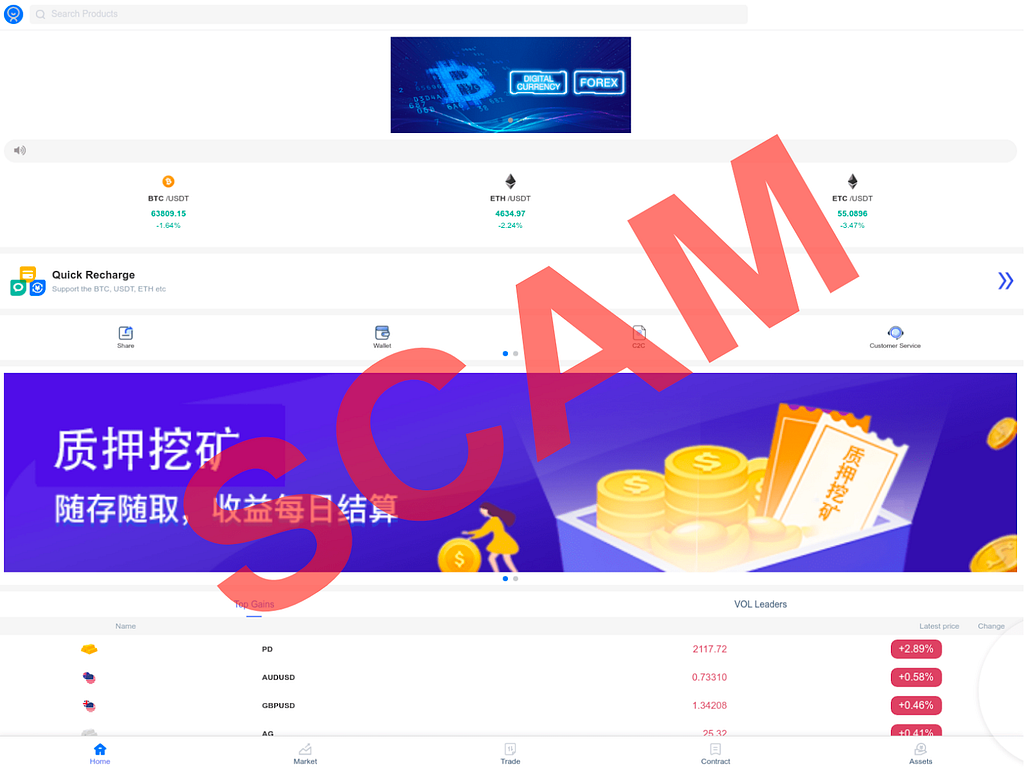
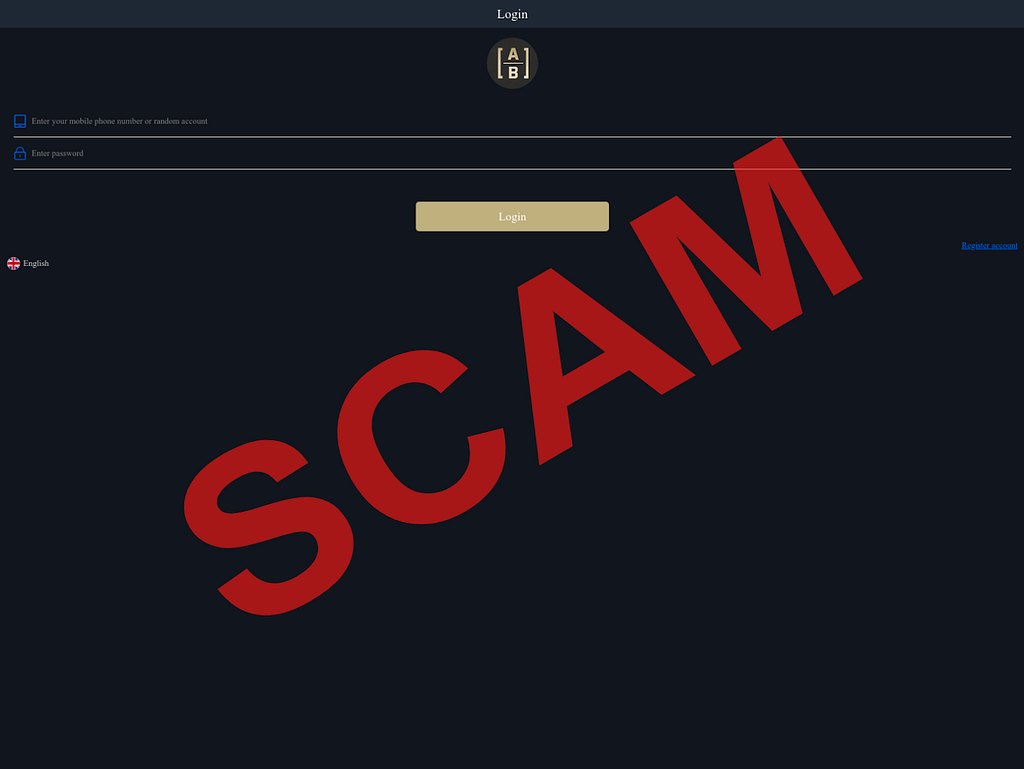
- Victims are directed to visit a fraudulent website that often looks like a legitimate trading platform and coached into depositing funds.
- Some victims even receive a small amount of funds that are claimed to be “returns” on their investment to entice them to invest even larger sums.
- When the victim tries to withdraw funds from the site, they are then often told they owe a tax payment or service fee before their funds will be released in an effort to further extort them for money.
How we have been working to protect our users:
- Teams across Coinbase work to identify and add addresses associated with scams to our products’ blocklists to aid in protecting our customers.
- Security teams frequently conduct scans to identify clusterings of existing scam sites and collaborate with law enforcement to enforce takedowns. These teams have increased monitoring to identify new sites that have the potential to be similarly abused.
- While it is impossible to predict all addresses associated with scams, we conduct blockchain analysis on known scam addresses to map out related wallets and we communicate with other exchanges to inform them when they may be receiving these scammed funds.
- We routinely collaborate with law enforcement to share intel on emerging scams and support their investigations into bad actors.
The following steps can be taken to protect yourself:
- Be skeptical of investment opportunities from people you meet through online forums or dating apps, even if you have been communicating for a while. If they claim to have an exclusive or urgent opportunity, this is a big red flag.
- Don’t disclose your current financial status to people you’ve met online and don’t post any of your financial information on social media.
- Independently research any trading platform you are considering sending money to, including using consumer protection websites.
- Please report any scams including the URL and the receiving cryptocurrency address to security@coinbase.com.
- If you become aware of a scam, please report it to the FBI’s Internet Crimes Complaint Center.
- Report any scam websites to Google Safebrowsing
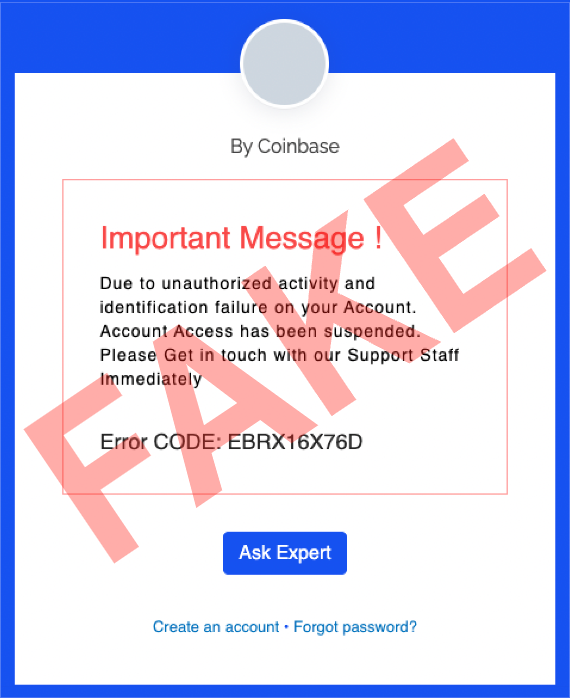
Investment scam landing pages often look like the following:
Security PSA: Sha Zhu Pan (Pig Butchering) Investment Scams was originally published in The Coinbase Blog on Medium, where people are continuing the conversation by highlighting and responding to this story.