
ZachXBT says a hacker has breached 15 crypto-focused X accounts to share scam memecoins that have netted the attacker around $500,000.
A threat actor has stolen around $500,000 over the last month from launching memecoin phishing scams on 15 compromised X accounts, according to blockchain investigator ZachXBT.
The perpetrator impersonated the X team and sent fake copyright infringement notices to create a sense of urgency and trick the social media platform’s users into visiting phishing sites, ZachXBT explained in a Dec. 24 X post.
The victims would then unknowingly use the fake site to reset their X account passwords and two-factor authentication (2FA) logins.

Twilio, the developer of the Authy authenticator app, said user phone numbers were leaked to attackers but accounts themselves were not compromised.
Hackers gained access to the Authy Android app database and “were able to identify data associated with [accounts], including phone numbers,” according to a July 1 security alert post issued by the app’s developer, Twilio.
The accounts themselves “are not compromised,” the post stated, implying that the attackers were not able to gain authentication credentials. However, the exposed phone numbers may be used for “phishing and smishing attacks” in the future. Because of this risk, Twilio encouraged Authy users to “stay diligent and have heightened awareness around the texts they are receiving.”
Related: What is a phishing attack in crypto, and how to prevent it?

The 2FA security measure is optional for Friend.tech users seeking additional security on the platform.
The team behind the decentralized social media platform Friend.tech has added a new security feature amid attempts to stem a flood of SIM-swap attacks targeting its users.
“You can now add a 2FA password to your Friend.tech account for additional protection if your cell carrier or email service becomes compromised,” the team explained in an Oct. 9 post on X (formerly Twitter).
Friend.tech users will be prompted to add another password in when signing onto new devices.
“Neither the friendtech nor Privy teams can reset these passwords, so please use care when using this feature,” Friend.tech added.
You can now add a 2FA password to your https://t.co/YOHabcBL3H account for additional protection if your cell carrier or email service becomes compromised.
— friend.tech (@friendtech) October 9, 2023
Neither the friendtech nor Privy teams can reset these passwords, so please use care when using this feature pic.twitter.com/g0m2E4att2
The latest change follows several SIM-swap attacks targeting Friend.tech users since September.
On Sept. 30, froggie.eth was among the first in a string of Friend.tech users to be compromised by a SIM-swap attack, urging others to stay vigilant.
got swim swapped for 20+ ETH (they drained my https://t.co/xb5o31p3Yy)... stay vigilant out there bros
— froggie.eth (@brypto_) September 30, 2023
set a PIN on your sim even if you don't think you need to
More Friend.tech users came forward with similar stories in the following days with an estimated 109 Ether (ETH), worth around $172,000, stolen from four users within a week. Another four users were targeted over a 24-hour period just days later, with another $385,000 worth of Ether stolen.
Friend.tech had already updated its security once on Oct. 4 to allow users to add or remove various login methods in an attempt to mitigate the risk of SIM-swap exploits.
Several observers criticized Friend.tech for not implementing the solution sooner.
“Finally,” one user said, while another said: “took you long enough.”
However, a prominent creator on Friend.tech, 0xCaptainLevi, was more optimistic, stressing that 2FA is a “big deal” and can help push the social media platform to unseen heights:
2FA is a big deal. Road to $100M TVL never seemed brighter❤️ https://t.co/bxd3V3M3mx
— Levi ⚡️ (@0xCaptainLevi) October 10, 2023
In an Oct. 8 X thread, Blockworks founder Jason Yanowitz revealed one of the ways the SIM-swap attacks are being orchestrated. The process involves a text message that asks the user for a number change request, where users can reply with “YES” to approve the change or “NO” to decline it.
If the user responds with “NO” — the user is then sent a real verification code from Friend.tech and is prompted to send the code to the scammer’s number.
“If we do not hear a response within 2 hours, the change will proceed as requested,” a follow-up message shows.
"In reality, if I sent the code, my account would get wiped," he said.
Someone is trying to hack my @friendtech
— Yano (@JasonYanowitz) October 8, 2023
1) Text sent saying they’re changing my number
2) I respond no
3) They say to confirm no, send the verification code
4) Receive actual verification code from friend tech
5) After no response, they text again saying they’ll auto… pic.twitter.com/j76vI969jP
Related: Friend.tech copycat Stars Arena patches exploit after some funds drained
The total value locked on Friend.tech currently sits at $43.9 million, down 15.5% from its all-time high of $52 million on Oct. 2, according to DefiLlama.

Cointelegraph reached out to Friend.tech for comment but did not receive an immediate response.
Magazine: Blockchain detectives — Mt. Gox collapse saw birth of Chainalysis

The firm has implemented additional security measures following an investigation that found “only a few” 3Commas user accounts were compromised.
Crypto trading bot provider 3Commas is on “heightened alert” after some of its user’s accounts were compromised and used to place trades.
An Oct. 8 blog post from 3Commas co-founder and CEO Yuriy Sorokin said it received reports from users concerning unauthorized trades on their accounts after resetting their passwords.
An investigation found “only a few customer accounts” were compromised and unauthorized trades made. 3Commas did not disclose the number of users affected.
Notice of Incident. We've identified a security incident that has come to our attention concerning the security of 3Commas accounts. Learn more and stay secure:
— 3Commas (@3commas_io) October 8, 2023
Read our Blog Post: https://t.co/sJmfzOJE49 pic.twitter.com/MRJ40D29pj
“We will continue with our investigation into this matter,” Sorokin wrote. “Please note, however, that in the meantime, our services are running normally, and we will continue to operate in a state of heightened alert.”
The accounts with unauthorized trades mostly had not enabled two-factor authentication (2FA), according to 3Commas. It said the data accessed did not include user API data or passwords.
As additional security measures, the firm said it implemented a new approach to resetting passwords and disabled API connections after a user resets their password. It recommended that users enable two-factor authentication and regularly change their password.
Related: OpenSea ‘unaware’ of any involvement of former exec in $60M rug pull
In December 2022, the firm disclosed an incident from that October where user API keys had been leaked, leading to unauthorized trades on victim accounts.
Sorokin and 3Commas initially denied a breach had taken place and instead suggested its customers had been phished. It later relented and Sorokin admitted there had been an API leak from 3Commas.
3Commas users affected by the API leak called for refunds and an apology for being gaslighted.
“We regret that such an incident has taken place,” said Sorokin on the latest incident. He added that 3Commas is improving its security to prevent or limit similar future incidents.
3Commas did not immediately respond to Cointelegraph’s request for comment.
Magazine: How to protect your crypto in a volatile market — Bitcoin OGs and experts weigh in
 General Bytes experienced a security incident on March 17 and 18 that enabled a hacker to remotely access the master service interface and send funds from hot wallets, according to the company and sources. The breach forced a majority of U.S.-based crypto automated teller machine (ATM) operators to temporarily shut down. The hacker was able […]
General Bytes experienced a security incident on March 17 and 18 that enabled a hacker to remotely access the master service interface and send funds from hot wallets, according to the company and sources. The breach forced a majority of U.S.-based crypto automated teller machine (ATM) operators to temporarily shut down. The hacker was able […]
While members of the crypto community are doubtful the lawsuit against Coinbase will be successful, it has sparked a conversation about the issues with SMS 2FA.
The crypto community is debating whether SMS two-factor authentication (2FA) should ever be used for account security following news that a Coinbase customer is suing the cryptocurrency exchange for $96,000.
On Mar. 6 Jared Ferguson filed a lawsuit against Coinbase in the United States District Court for the Northern District of California, claiming he lost “90% of his life savings” after funds were withdrawn from his account by identity thieves and Coinbase had refused to reimburse him.
Ferguson is said to have fallen prey to a type of identity theft known as “SIM swapping,” which allows fraudsters to gain control of a phone number by tricking the telecom provider into linking the number to their own SIM card.
This allows them to bypass any SMS 2FA on an account, and in this situation allegedly allowed them to confirm the withdrawal of $96,000 from Ferguson's Coinbase account.
Ferguson claimed he lost service after his phone was hacked on May 9, and noticed the funds had been taken from his Coinbase account after getting a new sim card and restoring his service as per instructions from his service provider T-Mobile.
T-Mobile was previously sued by a SIM-swapping victim in February 2021 following the theft of approximately $450,000 worth of Bitcoin (BTC).
Coinbase denied any responsibility for the hack of Ferguson’s account, telling him in an email that he is “responsible for the security of your e-mail, your passwords, your 2FA codes, and your devices.”
Related: Hacker returns stolen funds to Tender.fi, gets $97K bounty reward
Members of the crypto community were generally doubtful that Ferguson’s lawsuit would be successful, noting that Coinbase encourages the use of authenticator apps for 2FA rather than SMS and describes the latter as the “least secure” form of authentication.
I'm guessing his password was compromised because it was used on other sites, one of which got breached. Also, Coinbase encourages Authenticator app for 2FA by labeling it "secure" and SMS as "moderately secure".
— Dave Ferguson (@_sc0rn) March 7, 2023
Some Reddit users discussing the lawsuit in a post titled “Never Use SMS 2FA” went as far as suggesting SMS 2FA should be banned, but noted that it was the only authentication option available for many services, as one user said:
“Unfortunately a lot of services I use don’t offer Authenticator 2FA yet. But I definitely think the SMS approach has proven to be unsafe and should be banned.”
Blockchain security firm CertiK warned of the dangers of using SMS 2FA in September, with its security expert Jesse Leclere telling Cointelegraph that “SMS 2FA is better than nothing, but it is the most vulnerable form of 2FA currently in use.”
Leclere said dedicated authenticator apps like Google Authenticator or Duo offer nearly all the convenience of using SMS 2FA while removing the risk of SIM swapping.
Reddit users shared similar advice but added authenticator apps on phones also make that device a single point of failure and recommended the use of separate hardware authentication devices.
Siyu Liu, Senior Product Manager; Chetan Rane, Product Manager
Tl;Dr: We are excited to introduce the Coinbase Security Prompt: a faster and safer way for our users to verify their identity & activities when interacting with the Coinbase ecosystem.
https://medium.com/media/a37c2f6bc2331106e43db5223ea0bf4e/hrefAt Coinbase, we believe that our users need to have access to the best security possible without sacrificing ease and convenience. Providing a safe, secure, and easy-to-use platform that users trust is our continuous commitment to all of our current and future customers. That’s why, we require all Coinbase accounts to use 2-Factor Authentication (2FA). 2FA is a security layer on top of username and password. Accounts with 2FA enabled require users to provide their password (first “factor”) and a 2FA code (second “factor”) when signing in. While Coinbase offers both hardware key and authenticator app support on both web and mobile for 2FA, many customers appreciate the convenience of SMS.
Thinking about that, we’re now going one step further in keeping our users’ accounts secure via Coinbase Security Prompt, a simpler, faster and safer 2FA method that improves overall account security. How? Instead of sending an SMS code, the new Coinbase Security Prompt sends users a push notification to their Coinbase mobile app, asking if they are trying to sign in. Now with Coinbase Security Prompts, users can authenticate a login action with a simple tap on their phone:
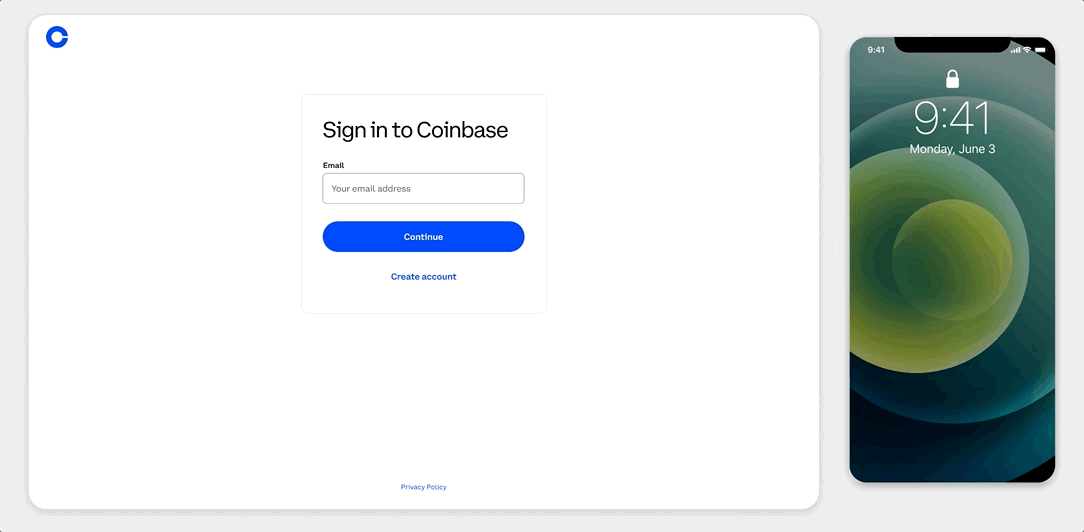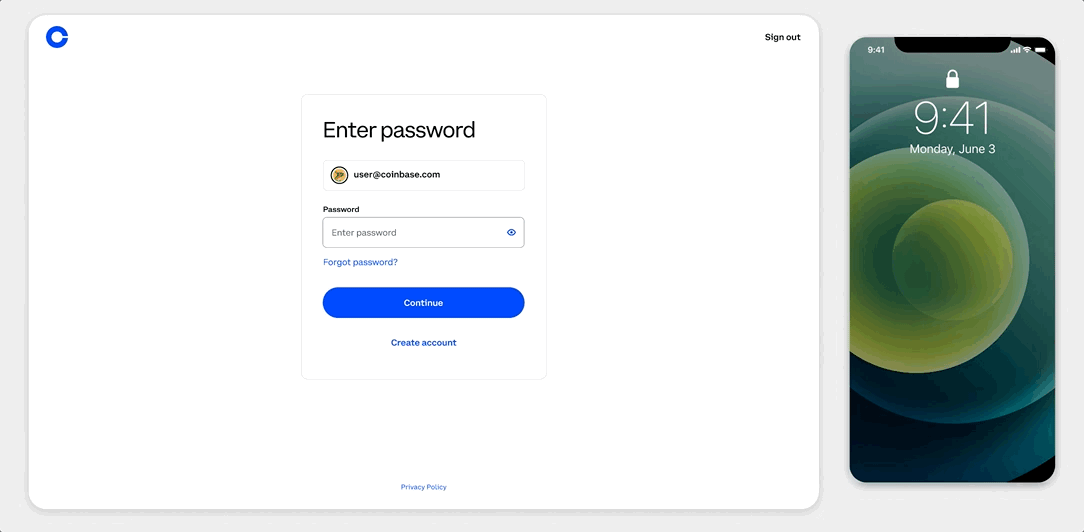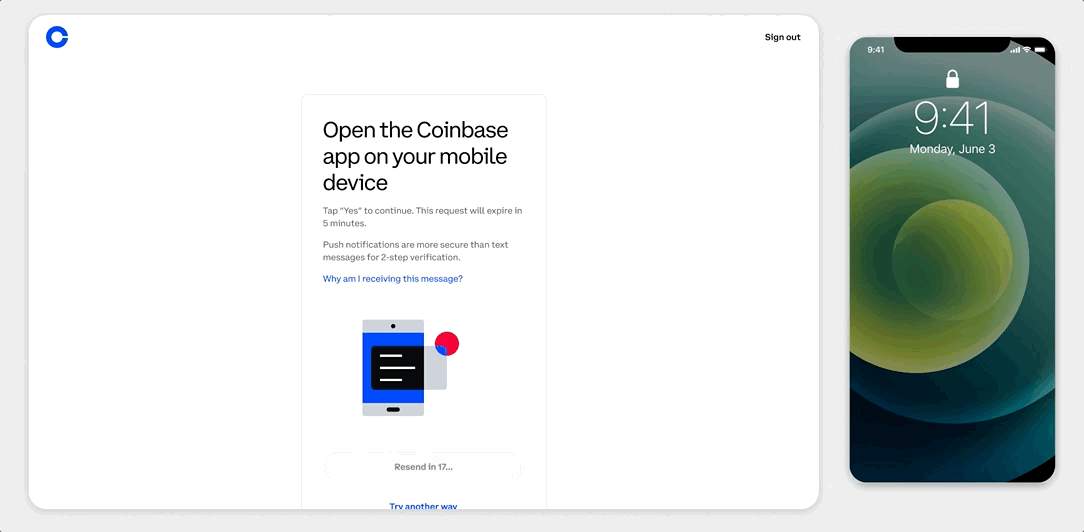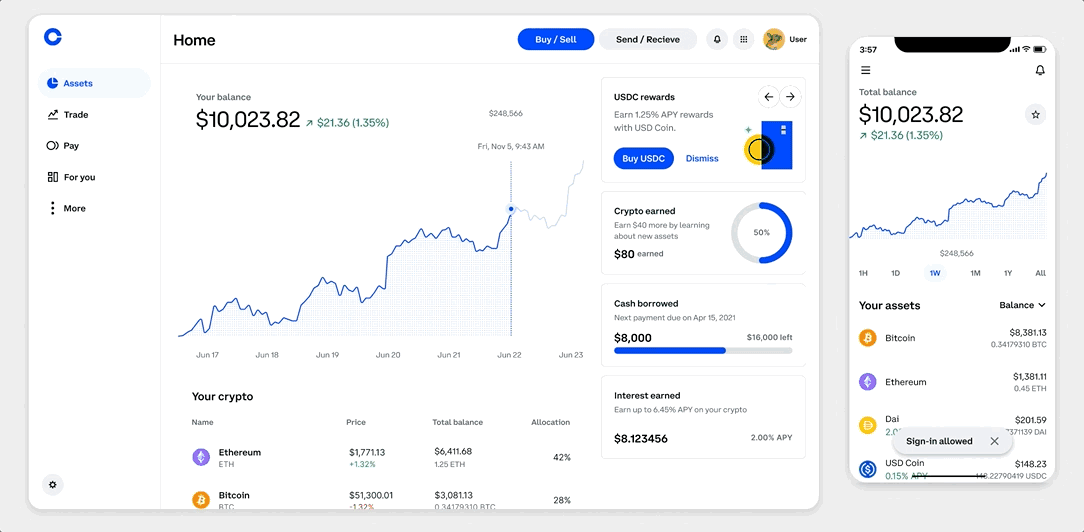
Our customers will automatically have a stronger security without losing the ease and convenience of using their phones, from anywhere. Security Prompt is resilient against SIM Swap attacks by removing the mobile carrier as an intermediary from the authentication process. It also reduces the risk of phishing attacks by providing detailed information about where the request is coming from, such as the location or browser type.
Starting in July through the rest of 2022, all of our eligible* users will gradually start to be automatically enrolled to complete their 2FA via Security Prompts. Users who are still receiving SMS codes as their 2FA method can get access to Coinbase Security Prompts by downloading the Coinbase app.
*Eligible users are those who have an active mobile login session, trying to login from a second device and are using our latest Coinbase app version.
Introducing Coinbase Security Prompt — a safer and easier way of signing into Coinbase was originally published in The Coinbase Blog on Medium, where people are continuing the conversation by highlighting and responding to this story.
 The Royal United Services Institute (RUSI), the British defense and security think tank, questions whether or not non-fungible token (NFT) assets can be used for money laundering purposes. The report determines that in order to mitigate the money laundering risks a ‘know your customer’ monitoring system “needs to be implemented.” RUSI: ‘NFT Technology Can Raise […]
The Royal United Services Institute (RUSI), the British defense and security think tank, questions whether or not non-fungible token (NFT) assets can be used for money laundering purposes. The report determines that in order to mitigate the money laundering risks a ‘know your customer’ monitoring system “needs to be implemented.” RUSI: ‘NFT Technology Can Raise […] Buda, a Chile-based cryptocurrency exchange, has started requesting selfie verification every time a user needs to withdraw funds to a new bitcoin address. This new measure now introduces a new layer of security for users to avoid getting their accounts hacked, but it will only be mandatory for those that don’t have 2FA activated. Buda […]
Buda, a Chile-based cryptocurrency exchange, has started requesting selfie verification every time a user needs to withdraw funds to a new bitcoin address. This new measure now introduces a new layer of security for users to avoid getting their accounts hacked, but it will only be mandatory for those that don’t have 2FA activated. Buda […]