By Paul Grewal, Chief Legal Officer
Tl;dr: At Coinbase, we take our responsibility to build a more open, accessible financial system very seriously. We’re deeply committed to our asset listing policies and processes, and we’ll continue to innovate as our dynamic space evolves.

A few weeks ago, we shared concerns about purchases of certain assets right before we announced they were being considered for listing on Coinbase — possibly using insider information. We take this issue very seriously and therefore wanted to share more about our efforts in this space.
The blockchain fundamentally drives greater transparency in financial transactions
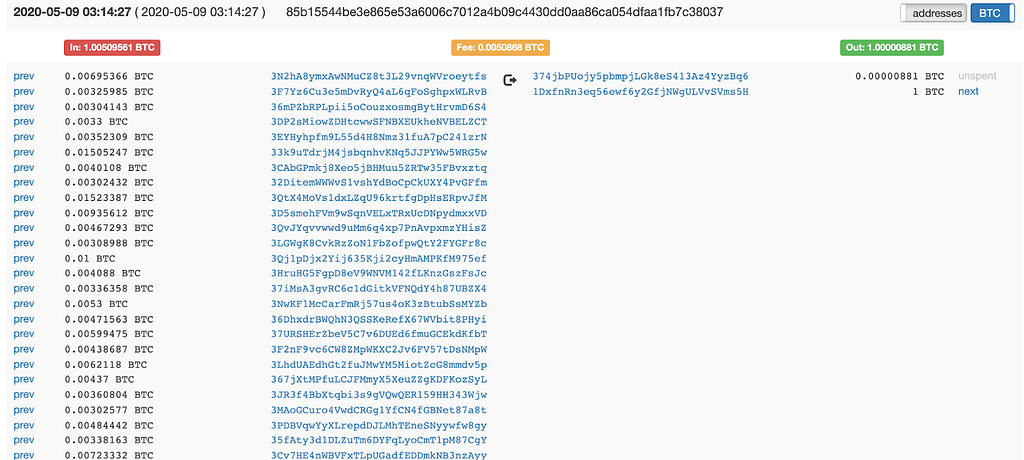
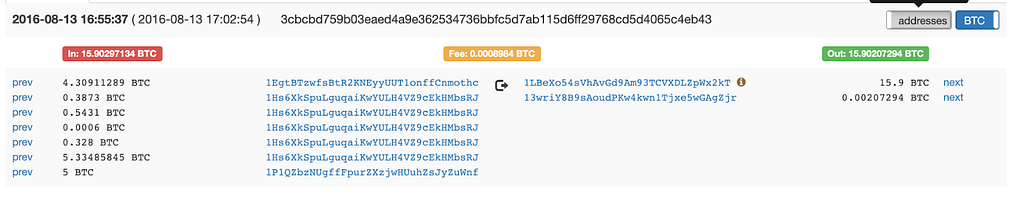
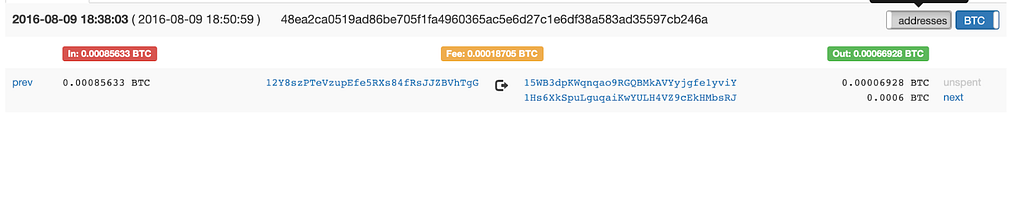
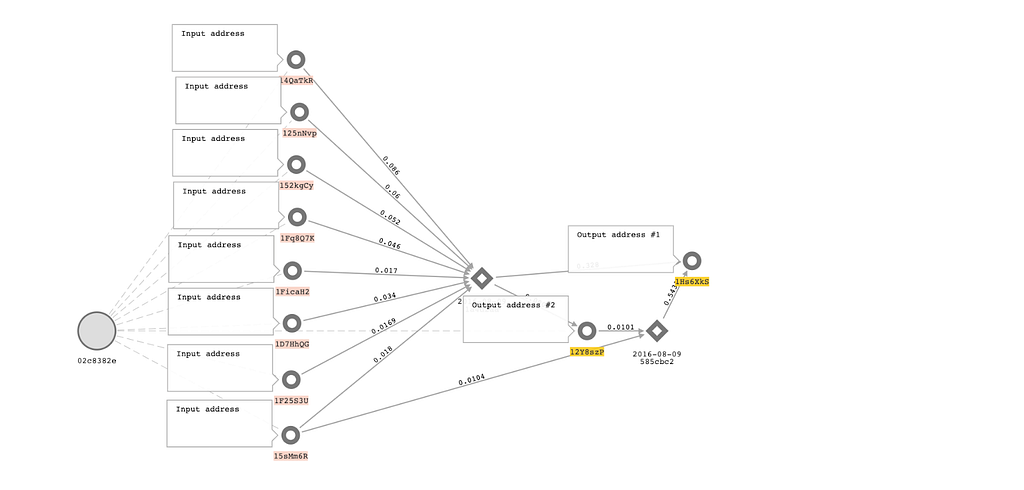
First, it’s important to understand that tracking and disrupting bad actors using crypto is far more effective than if they were using traditional fiat currencies. This isn’t to say that it’s easy, but we do have an advantage because crypto transactions are recorded on a permanent and public blockchain, which gives our investigation teams — along with the public and law enforcement — visibility into the details of different transactions. With crypto, it’s possible to trace and map transactions across users and exchanges — creating a fuller picture of what happened with any given trade, and making it easier to identify things that look like possible market manipulation or trades using material nonpublic information.
We have an exceptional team dedicated to preventing and identifying financial crimes
We have more than a decade of experience tracking and disrupting illegal activity, and have built expert teams to support these efforts along the way, including many with substantial experience in the public and private sector. In addition to our Security, Trade Surveillance, Global Investigations, and Special Investigations teams, we have a dedicated Financial Crimes Legal team. This team is led and staffed by multiple former federal criminal prosecutors and overseen by a former federal judge. Many of these former prosecutors have been part of some of the largest cryptocurrency cases in history, and are charged with making sure we’re doing everything we can to detect and disrupt bad actors.
Frontrunning can happen through technical or human means
Technical
The primary way we’ve seen information about possible asset listings become public before any announcement is through technical signals. For example, sometimes before onboarding an asset, we have to test it in ways that show up on the blockchain. These signals are not obvious to most, but are nevertheless accessible to all and may be detected if someone is looking hard enough for it, by examining on-chain data. That’s why we take steps to minimize this type of risk, including:
- Announcing planned asset launches once a decision has been made to list an asset, but before key technical integration work begins, so everyone has access to the same information.
- Exploring new ways of integrating and testing asset launches (including off-chain sandbox testing).
- Building and deploying industry-first analysis tools to test our systems using a wide range of techniques based on observed real-world behavior.
- Using a variety of best-in-class security tools to monitor and control access to sensitive listing information.
Human Sharing/Frontrunning
Information can obviously get out when people share it. Coinbase has gone above and beyond what a traditional financial institution can do to track and address this kind of bad behavior:
- Our Trade Surveillance and other teams leverage the public blockchain to detect prohibited or suspicious transactions and then trace those funds across wallets, users, and exchanges (in a way traditional finance can’t) to see who profited and understand their connections.
- We mandate that all employees trade crypto only on Coinbase’s trading platforms (where the asset is supported) so we can look out for prohibited trading activities.
In addition to Trade Surveillance, we also have more than 50 employees across various teams supporting the detection and prevention of illicit activity and misconduct, both on our platform and within the broader crypto ecosystem.
As we’ve stated multiple times, if an investigation finds that a Coinbase employee was involved in misuse of company information related to asset listings, we will not hesitate to terminate them — and, when appropriate, refer them to relevant law enforcement authorities.
We measure impact to drive accountability
It takes time to notice the effect of some of these changes, but we’re already seeing positive early indications of their impact on new asset launches.
Conclusion
To us, success is all market participants trading on the same information. That’s our goal. Crypto is a dynamic environment, so we are continually looking for additional ways to protect the confidentiality of information about our asset listings.
That’s why steps like these are so important. And while there’s always more work to do, I’m confident that we have the teams, resources, and experience to make Coinbase the most innovative and trusted way for people everywhere to access the cryptoeconomy.
Building a more open financial System: How Coinbase detects bad actors was originally published in The Coinbase Blog on Medium, where people are continuing the conversation by highlighting and responding to this story.