
New data from blockchain intelligence platform DappRadar reveals that $2.3 billion in funds have flowed into the crypto gaming sector in the first three quarters of 2023. In a new blog post, DappRadar says that investors see potential in blockchain gaming as $600 million flowed into the industry last quarter – leaving the sector atop […]
The post $2,300,000,000 in Investment Funding Flows to Blockchain Gaming in First Three Quarters of 2023: DappRadar appeared first on The Daily Hodl.
Dive into the world of Web3 development and learn how to create decentralized applications using ChatGPT.
The landscape of web development has undergone a profound transformation with the emergence of Web3 technologies. As blockchain and decentralized applications (DApps) gain momentum, developers are embracing this new paradigm to create a more open, secure and user-centric internet. This article will embark on a journey of learning Web3 development with the assistance of ChatGPT, exploring seven prompts that provide valuable insights and generated outputs.
A developer with a strong background in traditional web development, and who is curious about the shift to Web3 technologies, may utilize ChatGPT to learn Web3 development basics.

Web3 developers should learn smart contracts because they form the backbone of decentralized applications, enabling direct blockchain interaction and the creation of programmable assets and decentralized finance (DeFi) solutions. ChatGPT can help beginner Web3 developers learn about smart contracts at their convenience, free of cost and in a simplified way.

Related: 5 ChatGPT prompts for web developers
An experienced programmer who is looking to expand their skill set by exploring the realm of decentralized networks may utilize ChatGPT to learn the ins and outs of interacting with decentralized networks like Ethereum programmatically. Below is an example of a ChatGPT prompt that might be helpful.

With a solid understanding of web development concepts, developers who are eager to explore the unique intricacies and opportunities that come with building applications on blockchain platforms may use ChatGPT to transition into the world of decentralized technologies.

Recognizing the significance of decentralized identity solutions in the modern digital landscape, cybersecurity specialists keen on leveraging blockchain technology to enhance security measures may use ChatGPT to explore the role of decentralized identity in revolutionizing authentication and identity verification practices.

Related: What is decentralized identity in blockchain?
Web3 developers may utilize ChatGPT to learn best practices that encompass a set of guidelines and strategies to ensure the secure, efficient and user-friendly creation of DApps and protocols using blockchain and decentralized technologies.

As developers delve into the world of Web3, understanding the emerging trends is crucial for staying ahead of the curve and building innovative applications. As a result, they may use ChatGPT to be aware of future trends in Web3 development.

As the world of Web3 development continues to evolve, leveraging resources like ChatGPT for insights and guidance can greatly accelerate your learning journey. From understanding the basics of blockchain to diving into advanced topics, the collaboration between human curiosity and AI assistance can pave the way for innovative contributions to the decentralized future.

Explore five critical smart contract vulnerabilities that pose risks to blockchain systems. Learn how to spot and neutralize these threats for secure and resilient DApps.
Smart contracts, the self-executing code on blockchain platforms, have transformed industries by automating processes and enabling trustless transactions. However, their complexity can also make them susceptible to vulnerabilities that could be exploited by malicious actors.
This article will delve into five common smart contract vulnerabilities, explore their potential impacts, and provide insights into how to identify and mitigate them effectively.
Reentrancy occurs when an attacker repeatedly calls a vulnerable smart contract function before the original transaction is completed. This can lead to unexpected behavior and result in the contract losing funds. To mitigate this, ensure that the contract’s state changes are made before interacting with external contracts and implement checks to prevent multiple calls.
Integer overflow or underflow happens when a variable exceeds its maximum or minimum value. Attackers can exploit this to gain control over the contract. Use safe math libraries to handle arithmetic operations and prevent these vulnerabilities from occurring.
Flaws in access control can grant unauthorized users the ability to manipulate the smart contract. To address this, adopt the principle of least privilege, limiting access to sensitive functions and data only to authorized users. Implement robust authentication mechanisms to prevent unauthorized access.
Related: What is a smart contract security audit? A beginner's guide
Smart contracts sometimes interact with external contracts. If not properly validated, these external calls can introduce security risks. Implement strict validation checks and use interface contracts to interact with external contracts, reducing the potential attack surface.
Bugs in the contract’s code can create vulnerabilities. Thoroughly audit and test the code using security tools and techniques. Engaging professional third-party auditors can help identify potential vulnerabilities and provide recommendations for improvement.
Smart contract vulnerabilities pose a significant risk to blockchain ecosystems and digital assets. By understanding these vulnerabilities, adopting secure coding practices and leveraging auditing and testing tools, developers can minimize the chances of exploitation.
A proactive approach to identifying and mitigating these vulnerabilities is essential for ensuring the robustness and security of smart contracts in a rapidly evolving blockchain landscape.

Discover the contrasting functions of DApps and protocols in the blockchain world, and gain insights into how they contribute to the growth of decentralized technologies.
In recent years, the rise of blockchain technology has paved the way for groundbreaking innovations in the realm of decentralized systems. Among the revolutionary concepts are decentralized applications (DApps) and protocols. While both are integral components of the decentralized ecosystem, they serve distinct purposes and play different roles.
This article explores the contrasting characteristics of DApps and protocols, shedding light on their respective functionalities and importance in the world of decentralized technologies.
Software programs that run on a decentralized network of computers rather than a centralized server are known as decentralized applications or DApps. They make use of blockchain technology to guarantee immutability, security and transparency.
Like traditional applications, DApps are designed to have front-end and back-end components. Users can interact with the application using the front-end interface, while the back-end, also known as the smart contract, is deployed on the blockchain. The smart contract executes the application’s logic and securely handles data.
The decentralized structure of DApps sets them apart. As a result, there is no single point of failure because they do not rely on a single organization or central authority. The blockchain network distributes transactions and data, making them unchangeable and censorship-resistant.
Related: What is DeFi? A beginner's guide to decentralized finance
Protocols, in the context of blockchain and decentralized technologies, refer to the underlying sets of rules and standards that define how the network operates. They provide the foundation for DApps to function and communicate effectively within the ecosystem.
The rules for data validation, consensus processes, and the network’s node-to-node communication protocol are all established via protocols. They make sure that everyone follows the same rules and can rely on the data exchanged within the system.
Related: Is blockchain technology ready for high-storage applications?
DApps are end-user applications that provide specific services and functionalities within the decentralized ecosystem. Protocols, on the other hand, serve as the underlying rules and standards that govern the entire decentralized network and enable seamless interactions between DApps.

Overall, DApps and protocols are driving the revolution toward a decentralized future, transforming various sectors and fostering innovation in the blockchain space.
Collect this article as an NFT to preserve this moment in history and show your support for independent journalism in the crypto space.

Intent-centric blockchain protocol Anoma secures $25 million in funding to continue developing its third-generation architecture.
Swiss nonprofit Anoma Foundation has secured a significant funding boost to continue the development and research of its third-generation blockchain architecture.
A third fundraising round secured $25 million for the organization, which is building what it describes as a generalized intent-centric blockchain architecture. The technology is touted to enable the development of completely decentralized applications (DApps) and services, ranging from decentralized exchanges (DEXs) to blockchain rollup protocols.
Anoma co-founder Adrian Brink told Cointelegraph that its third-generation architecture offers more composability and ease of use than existing smart contract protocols like Ethereum and its Ethereum Virtual Machine (EVM).
Brink highlighted the evolution of blockchain systems, with Bitcoin (BTC) being the first generation of scriptable settlement architectures. Ethereum became the second generation with programmable settlement architecture, while Anoma looks to further the decentralization of existing blockchain-based applications and platforms:
“Anoma is the first architecture that is intent-centric, marking the third generation of architectures that contrast with the current transaction and blockchain-centric architectures.”
Its latest fundraising round is earmarked to support ongoing development and research initiatives for Anoma’s architecture as well as developer tools for its ecosystem.
Related: A beginner’s guide to understanding the layers of blockchain technology
Brink highlighted Anoma’s primary design principle of intent-centricity, which enables fully decentralized versions of existing DApps, such as rollups; nonfungible token (NFT) marketplaces like OpenSea and Flashbots; and decentralized exchanges that possess centralized components and limited on-chain settlement functions:
“It enables applications that are impossible to build on existing smart contract protocols, such as fully decentralized Gitcoin, Plural Money, Collaborative Finance, Multidimensional DAOs, runtime rollups, or multiparty multivariate bartering.”
Brink describes Anoma’s intent-centric design as a radically new take on how the industry architects decentralized systems, in contrast with transaction or blockchain-centric approaches like Bitcoin, Ethereum and other blockchains.
A July 2022 report from Chainalysis highlighted the landscape, with Algorand, BNB Chain and Avalanche emerging as competing layer-1 competitor chains to Ethereum looking to provide greater scalability or security.
Multitudes of layer-1 blockchains have been designed in the mold of Bitcoin and Ethereum, powering transaction and smart contract functionality.
Magazine: Bitcoin is on a collision course with ‘Net Zero’ promises
 As the Bitcoin Cash enthusiasts brace themselves for the much-awaited upgrade that vows to unleash decentralized applications, General Protocols revealed a complete production release of its decentralized hedging application, boasting a doubled contract size. Meanwhile, those utilizing the privacy-boosting protocol Cashfusion have fused over 17.4 million bitcoin cash since its inception, equivalent to a staggering […]
As the Bitcoin Cash enthusiasts brace themselves for the much-awaited upgrade that vows to unleash decentralized applications, General Protocols revealed a complete production release of its decentralized hedging application, boasting a doubled contract size. Meanwhile, those utilizing the privacy-boosting protocol Cashfusion have fused over 17.4 million bitcoin cash since its inception, equivalent to a staggering […]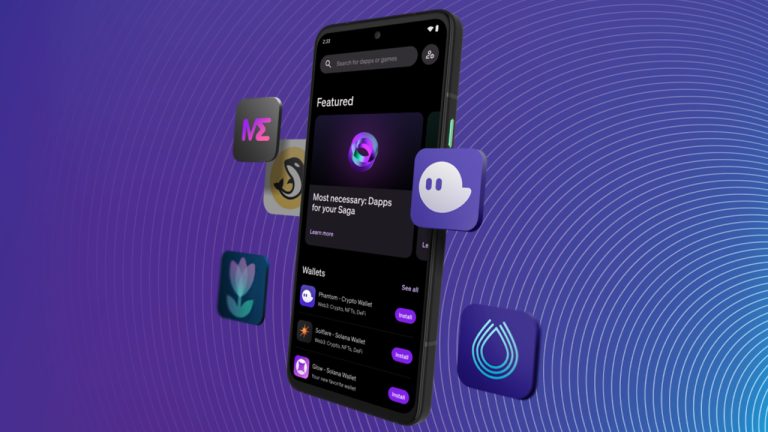 Solana’s cryptocurrency and Web3 smartphone, Saga, will be available for purchase on Monday, May 8, 2023. Crafted by OSOM, the Android smartphone is designed specifically for Web3 applications and enables users to self-custody crypto assets using its Seed Vault feature. Solana Smartphone Saga Ready for the Masses Solana Labs, Inc., the company behind the Solana […]
Solana’s cryptocurrency and Web3 smartphone, Saga, will be available for purchase on Monday, May 8, 2023. Crafted by OSOM, the Android smartphone is designed specifically for Web3 applications and enables users to self-custody crypto assets using its Seed Vault feature. Solana Smartphone Saga Ready for the Masses Solana Labs, Inc., the company behind the Solana […] In the past 20 days, the Arbitrum blockchain has recorded a significant number of transactions coinciding with the recent ARB airdrop that occurred on March 23. About two weeks ago, on that day, the Arbitrum network recorded an all-time high of 2.72 million transactions settled in 24 hours. L2 Network Arbitrum Records 2.72 Million Transactions […]
In the past 20 days, the Arbitrum blockchain has recorded a significant number of transactions coinciding with the recent ARB airdrop that occurred on March 23. About two weeks ago, on that day, the Arbitrum network recorded an all-time high of 2.72 million transactions settled in 24 hours. L2 Network Arbitrum Records 2.72 Million Transactions […] On April 3, 2023, the Dfinity Foundation, a development team behind the Internet Computer (ICP) network, announced the launch of a native ICP token called “chain-key bitcoin” or “ckBTC.” The bitcoin derivative is backed 1:1 with the leading cryptocurrency asset. On Monday, Dfinity detailed that the technology “builds on the protocol-level integration with the Bitcoin […]
On April 3, 2023, the Dfinity Foundation, a development team behind the Internet Computer (ICP) network, announced the launch of a native ICP token called “chain-key bitcoin” or “ckBTC.” The bitcoin derivative is backed 1:1 with the leading cryptocurrency asset. On Monday, Dfinity detailed that the technology “builds on the protocol-level integration with the Bitcoin […]
Metamask is rolling out a new update for its mobile app and browser extension that fixes the privacy issues that users encounter when using the popular crypto wallet. In a statement, Metamask says that the new MetaMask mobile now allows users to choose which account in their wallet should be associated with a decentralized application […]
The post MetaMask Enhances Privacy With Mobile DApp and Browser Extension Upgrades appeared first on The Daily Hodl.