Cypher Protocol freezes smart contract after an estimated $1M exploit

A crypto wallet suspected to be tied to the exploit shows it gained over $1 million in SOL and UDSC since the attack.
Solana-based decentralized futures exchange Cypher Protocol halted its smart contract after an estimated $1 million exploit.
On Aug. 7, Cypher alerted its 13,500 followers on X (formerly known as Twitter) that it had experienced a security incident and had thus frozen its smart contract.
The team added it is investigating the cause of the exploit and has reached out to the hacker to negotiate a potential return of stolen funds.
Cypher has has experienced an exploit/security incident. The smart contract has been frozen.
The team is currently working with individuals and investigating
To the hacker: We are writing to see whether you would be open to speaking with us about any potential next steps.
— cypher ©️ (@cypher_protocol) August 7, 2023
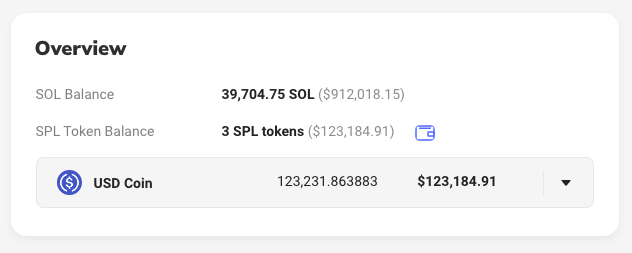
According to data from Solana blockchain explorer Solscan, the wallet suspected to be tied to the exploit stole approximately 38,530 Solana (SOL) tokens as well as $123,184 USD Coin (USDC) — netting a total of $1,035,203 in illicitly gained funds.
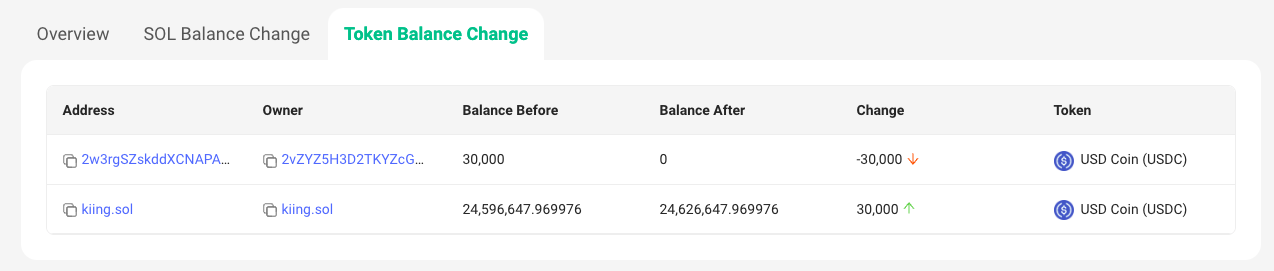
In the hours following the exploit, the alleged wallet transferred 30,000 USDC to Binance’s Solana USDC address “kiing.sol” in a possible attempt to cash out the stolen funds.
Related: ‘All funds are at risk’ — Steadefi exploited in ongoing attack
At the time of publication, the alleged hacker has yet to bridge any Solana-based funds to the Ethereum network.
The attack comes amid Cypher Protocol’s mtnDAO hacker house event, which it co-hosts with fellow Solana protocol Marginfi. Marginfi wrote in its Telegram that it remains independent from Cypher and had not been impacted by the attack.
Cointelegraph has reached out to Cypher Protocol for more details but did not receive an immediate response.
This is a developing story, and further information will be added as it becomes available.
Deposit risk: What do crypto exchanges really do with your money?
Go to Source
Author: Tom Mitchelhill